Geek Out with Purpose: January 8th Edition
January 8, 2016
In 2016, we are excited to bring you a new blog series called “Geek Out with Purpose” from our very own Purpose Tech team. These proud geeks will be sharing the latest and greatest tech for good news, explaining tech lingo and current events to make them more accessible to non-techie and techie types alike, and sharing those awe-inspiring visuals (think infographics, GIFs, and so much more) that only sound data and technology can bring us.
Without further ado, we bring you the first installment.
ARTICLES OF INTEREST:
10 Tech Tools to Help You Crush Your New Year’s Resolutions Highlighting the finding that a mere 8 out of the 45% of Americans who make resolutions are successful in achieving them, TNW News brings us the apps and services promising to maximize our efforts that received funding in 2015. Yes please!
This Angel Investor’s Solution to Gun Violence In the wake of a year stained with horrific gun violence, Inside Philanthropy sheds light on Smart Tech, a foundation focused on providing grants to businesses dedicated to improving gun safety. Supporting firearm technology that may lead to a decrease in accidental shootings and shootings committed by those who do not own the firearm, Smart Tech is issuing prize money to organizations who come up with the most impressive innovation. Categories for a $1 million award include limiting the use of guns to their actual owners, data-driven approaches to gun use, technology for enhanced community safety, and the promotion of brain health.
Trump Quietly Builds A Data Juggernaut Acquiring a team of experienced data strategists, Politico reports on Trump’s efforts to persevere amongst his rivals. While being criticized for a data program less robust than most, the campaign is now pushing to integrate information collected through the website, voter rallies, on unregistered or nontraditional supporters and also includes data from the RNC. “The very existence of the Trump data program undermines the assumption that his campaign is uninterested in ― or unaware of ― the basic technological infrastructure needed to identify and mobilize voters. Such tools, used so effectively by Barack Obama during his two presidential campaigns, could be especially critical for Trump as he seeks to increase turnout among new or untraditional GOP voters.”
Why The Bernie Breach Isn’t About Technology, And What’s At Stake: A must-read piece by Purpose CTO Josh Hendler who shares his take on the Bernie Breach and its implications. Josh offers some interesting commentary based on his previous experiences leading the DNC data program for several years then serving as the Technology Director from 2010–11. While at the DNC, Josh was part of a team that created the programs at the core of this debate: a uniform agreement with state-parties for data sharing, a national contract with the VAN (now NGPVAN), and Presidential candidate access.
TECH TIDBIT:
EYE CANDY:
The Best Tech GIFs of 2015:
The first 3-D printer able to squirt molten glass through a nozzle (read more)
As promised, this week we’ll wrap up our look at social engineering hacks with a look at phishing: using email, websites, texts, phone calls to gather personal information and gain access to systems by posing as a trustworthy entity.
What do Britney Spears, Barack Obama and Stephen Fry have in common? Their Twitter accounts were taken over by hackers through phishing. The hackers sent emails that looked like they were from Twitter with a link to a form that collected their login details. Once they gained access to the accounts, they sent spammy and amusing tweets such as the following tweet from Obama’s account: “What is your opinion on Barack Obama? Take the survey and possibly win $500 in free gas.”
Phishing is also a common tactic used to trick folks into downloading malevolent programs (malware). The programs may download as an email attachment, or after clicking a link for example. We’ll review malware in the next newsletter, but don’t wait to enjoy this story from Radiolab about a piece of malware and its highly entertaining victim.
There are a couple of straightforward things you can do to defend yourself against phishing.
-
Never click on links in emails or texts, go to the website manually and log in
-
Pay attention to website urls: look for misspellings or different domains (chase.net instead of chase.com for example)
Additionally, the defenses detailed in the last newsletter apply, particularly:
-
Use 2-factor authentication everywhere it’s available
-
Use a dedicated email account for account recovery
-
an email account tied to other services for account recovery can often be revealed to hackers, providing them with a high-value target
-
-
Do not use the same email prefix across accounts (porp@gmail.com, porp@me.com), they are easy to guess
-
Use different and strong random passwords for each of your accounts
-
Use a password manager like Meldium which is better for teams or OnePassword
-
-
Guard information from unfamiliar folks and verify their identity:
-
Do not provide personal or organizational information over the phone, ask for their name and callback number
-
Do not provide personal/organizational info via email, text, etc: contact them independently to verify the request
-

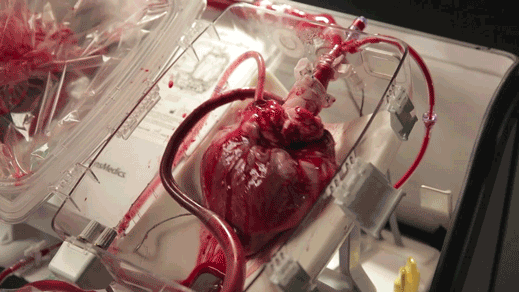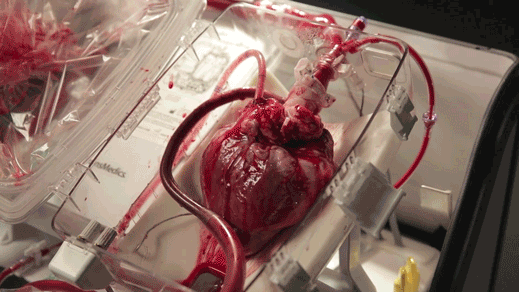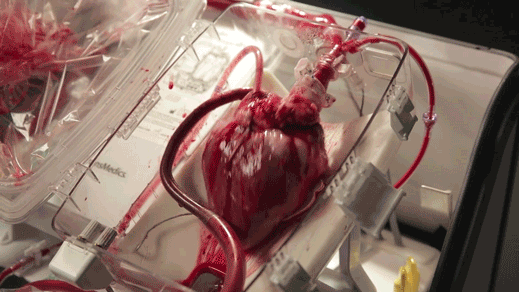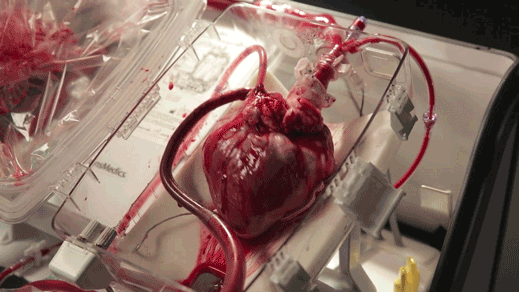
A device keeps hearts alive and beating outside the body (read more)
VR headset lets man inhabit teddy bear (read more)

Single human cells captured in bubbles for genomic analysis (read more)
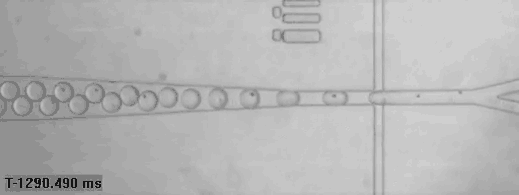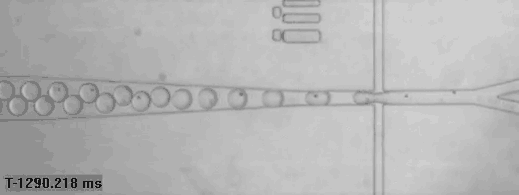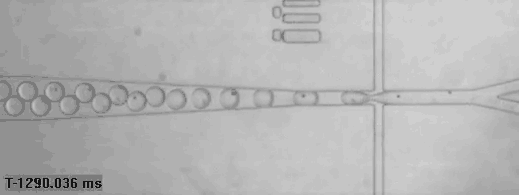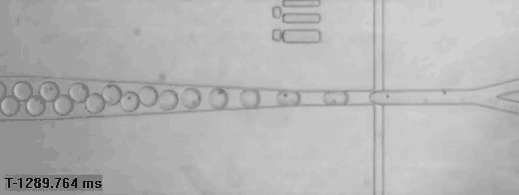
A bricklaying robot works three times as fast as a human (read more)

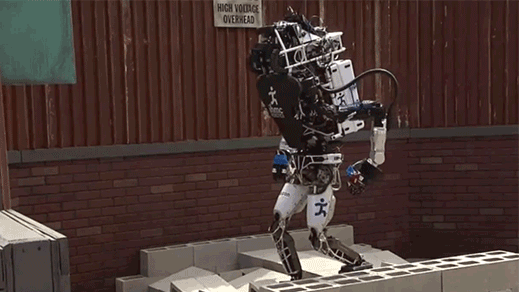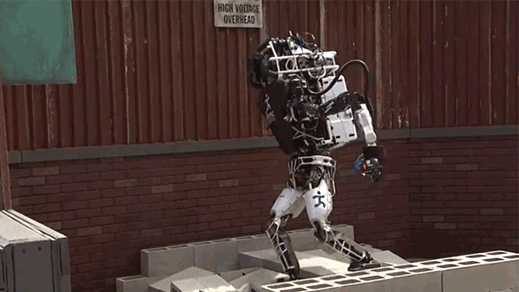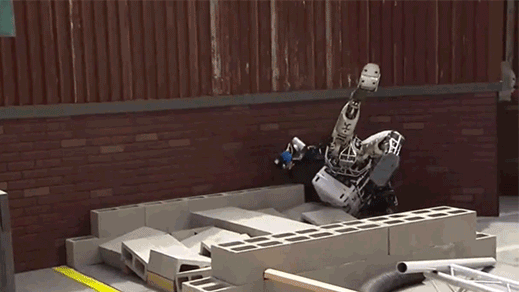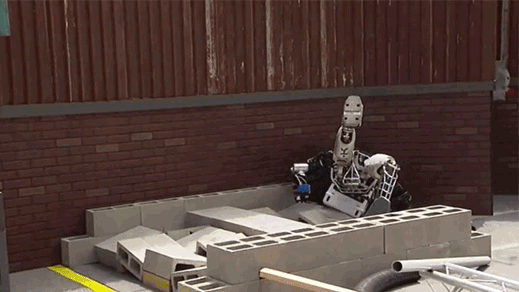
Scary humanoid robots that just fall over (read more)
for Equity & Evidence